April 2019 | Point of View
Building a cyber resilience framework to prevent business disruption
Take a fresh approach to cybersecurity that protects your business from today’s threats—and tomorrow’s
- Business operations matter more than data. First and foremost, your customers rely on your company to deliver the services and products they need. Cyberattacks not only implicate customer data but more importantly, disrupt service delivery. Therefore, prolonged service disruptions do far more damage to customers than data breaches alone.
- A company’s focus should be on response and resiliency, not full-stop prevention. The event of a cyberattack is now increasingly likely in today’s business environment: Malware attacks are costing businesses billions of dollars in lost revenue, operational shutdowns, and reputational damage. The best way to deal with inevitable security incidents and breaches is to make your network and your business resilient.
- Despite the escalated rate and severity of cyberattacks, leaders at most companies have not changed their approach to cybersecurity. Cybersecurity is not an IT issue or something that can be solved with more money—it takes a true companywide effort and culture change to address properly. In truth, many areas for improvement are operational: a lack of proper planning and preparation, siloed teams without insight into systemwide operational interdependencies, etc.
- Leadership teams must recognize the question of cybersecurity resilience for what it is—a foremost priority for long-term investment. Adopting a cyber resiliency mindset will have you reconfiguring teams, creating new action plans, and implementing regular system tests and drills. Resilience is about redundancy and protection, often at the cost of convenience. It is inconvenient for employees to log in with multi-factor authentication but doing so reduces the company’s risk substantially.
Introduction
Imagine starting your workday and all the systems that operate your business are unavailable. No email. No phones. No customer relationship management system.
Your employees look to you for leadership when they are unable to interact with customers, manufacture products, or deliver services. And, the CMO just called to say you are getting slammed on social media because your website is down.
When you finally get ahold of your IT leadership team, they inform you that all of your corporate data and systems have been infected and encrypted by malware. The attackers who claim to have the decryption key are asking for $1 million. Your CIO advises that you pay the ransom, because you have no other way to recover the data—but warns you that there is no guarantee the data can be recovered, even if you receive the key.
This is a nightmare scenario for a corporate leader, but one that is increasingly real. It happens every day to businesses of all sizes, in all industries, in private and public sectors. It is the reason that cybersecurity threats are the top business concern for CEOs in the United States.
Data, along with its connected systems and networked technologies, have become the lifeblood of modern business. They fuel the engines of businesses by creating efficiencies, connections, and profits. And while the value of digitized data and systems is well understood, the dependency caused by their ubiquity reveals a hidden weakness: What happens when those systems grind to a halt?
At West Monroe, we work with executives who are highly attuned to protecting personal data because it is what customers expect and compliance requires. Data breaches have flooded the headlines and avoiding them has become the No. 1 concern for most.
The truth is, focusing on data protection and security alone does not lead to a satisfactory defense—and it is frustrating executives who continue to see their cybersecurity spend rise without much return for their investment. Too much of the focus, we see, is on technology and tools, cost and spending, data and insurance. Not nearly enough of the focus is on people, robust cyber resilience strategies, continuity of business operations, documenting and practicing incident response plans, and spend that drives value.
In other words, it’s time to purge your preconceived notions about cybersecurity and take a fresh approach to cybersecurity that protects your business from today’s threats—and tomorrow’s. Resiliency is now the mandate.
The truth is, focusing on data protection and security alone does not lead to a satisfactory defense – and it is frustrating executives who continue to see their cybersecurity spend rise without much return for their investment.
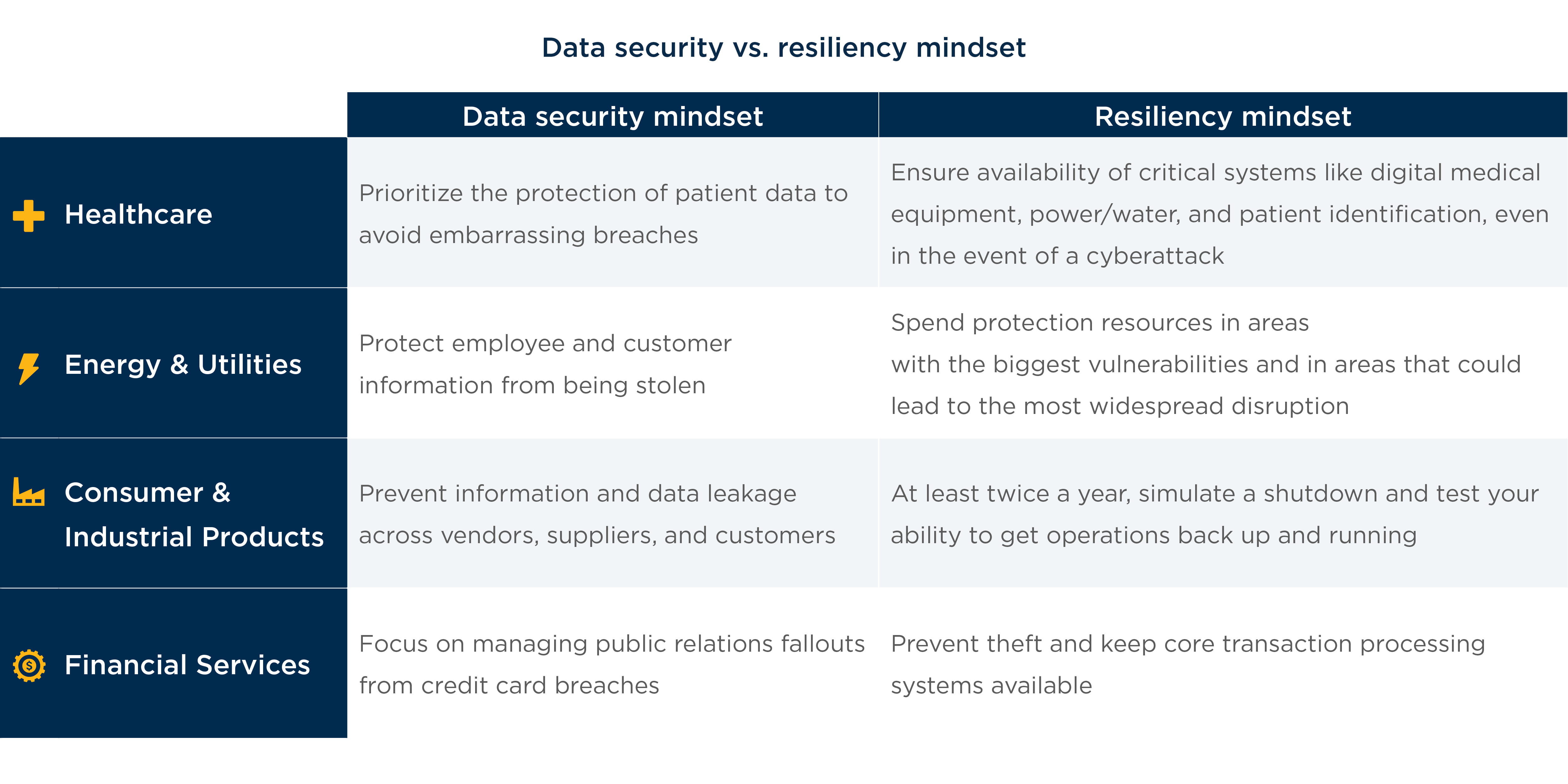
Chapter 1: Most executives underprioritize resiliency and overprioritize data security
Whether the cause is natural disaster or a ransomware attack, what happens if all networked operations— phone, email, e-commerce, cloud software—algorithms, and data-dependent analytics of your business cease to function?
The business case for long-term planning and increased investment in a holistic cybersecurity vision—designed to build and maintain operational resiliency—is both imperative and urgent.
Why business operations matter more than data
First and foremost, your customers rely on your company to deliver the services and products they need.
Cyberattacks not only implicate customer data but more importantly, disrupt service delivery. Therefore, prolonged service disruptions do far more damage to
customers than data breaches alone. It’s easy to see how these priorities play out. Ask yourself: Would you prefer a hospital that is able to treat you during a medical emergency, or one that suffers system failure? What’s more important: breach of your personal data or days without running water, heat, and power?
The cybersecurity threat is twofold—an increase in the frequency, severity, and sophistication of ransomware attacks coupled with insufficient cyber resiliency preparation at most firms. In other words, the malware will cause an infection, but an insufficient cyber resiliency response is how the attack spreads, leading to business disruption.
The event of a cyberattack is now increasingly likely in today’s business environment. Malware attacks are wreaking havoc on the international economy and costing businesses billions of dollars in lost revenue, operational shutdowns, and reputational damage. It’s likely that you may have even experienced an episode like this already at your company: Current industry research indicates that 50% of surveyed executives reported experiencing disruptions from malware six to ten times over the last five years.
Cyber Resilience Best Practices: It’s about preparation for attack recovery—not prevention
The best way to deal with inevitable security incidents and breaches is to make your network and your business resilient. This means taking a company-wide, high-level approach to evaluating the interdependencies and vulnerabilities within your network. It means running scenarios, testing backup solutions, communicating with staff, and prioritizing budgets and engagement with the board of directors.
Resilience is your ability to bounce back—and bounce back quickly.
And yet, too many executives view cybersecurity as a discrete data security problem. Too few perceive it as an operational threat to their business. In the worst cases, it’s simply a compliance box to check.
But consider that when cybercriminals take down or breach critical systems, the risk to your business goes far beyond stolen data, possible fines, or momentary customer displeasure. When a cyberattack happens, being caught flat-footed and ill-prepared to deal with it means prolonging a period of operational shutdown, lost revenue, unforeseen legal and technical costs, communication chaos, and most crucially, canceled services and missed expectations for customers.
The first step toward adopting a resiliency mindset is understanding that the goal is not to simply protect customer data, but to ensure continued operations and service delivery. ”
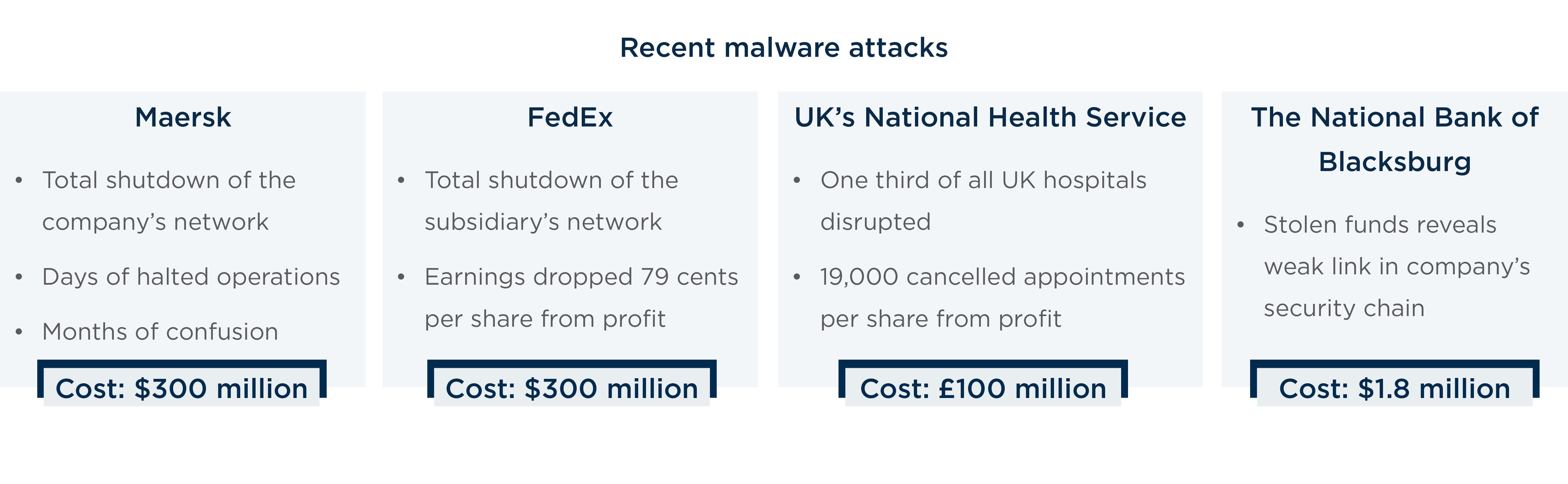
Maersk paid large sums to maintain customer trust
In June 2017, malware dubbed “NotPetya” infected Maersk, the international shipping giant responsible for 20% of global shipping container trade. The attack caused a total shutdown of the company’s network, grinding operations to a halt for days and sowing confusion and chaos for months afterward.
The disruption to Maersk’s operations affected the delivery of food, pharmaceuticals, and other goods around the world. Leading up to the attack, as documented in interviews investigating what went wrong, it became clear the company understood where the vulnerabilities were in its network, and yet didn’t prioritize the upgrades that would have protected against the attack that crippled its systems.
For Maersk, it cost $300 million. The company had to pay dearly to maintain customer relationships by liberally covering the costs of storage or other shipping methods. One Maersk customer received a seven-figure check from the company to cover the cost of sending his cargo via last-minute chartered jet. “They paid me a cool million with no more than a two-minute discussion,” he told Wired magazine.
FedEx's stock plunged
NotPetya also struck a FedEx subsidiary, ultimately costing parent company FedEx close to $300 million, nearly all stemming from lost revenue while the company’s operations were shut down by the virus. It was the second time the company had experienced devastating cyberattacks; WannaCry had infected FedEx earlier in 2017.
The company said the cyberattack slashed 79 cents per share from its profit—nearly 40 times the 2 cents per share caused by deadly Hurricane Harvey, which brought catastrophic flooding to southeastern Texas.
UK’s national health service could not treat patients
When a hospital’s systems shut down, real lives are on the line. In perhaps the most devastating, life-threatening ransomware attack we’ve seen, the WannaCry attack in May 2017 led to an intolerable disruption of care for one- third of the hospitals in the UK and the cancellation of 19,000 appointments for the United Kingdom’s National Health Service, costing the NHS almost £100 million.
Virginia bank lost millions from an opened word document
In January 2017, $1.8 million was stolen from The National Bank of Blacksburg, the second cyberattack by the same criminals who targeted the bank eight months prior. The technical forensics investigation after the last incident revealed the attackers accessed the system with a single, malicious Word document.
Chapter 2: Attackers are more sophisticated and well-funded, but corporate strategies haven’t caught up
By nature, cybersecurity threats are always changing and constantly in flux. But in examining the most damaging and dramatic attacks to date, we see a clear trend toward weaponized ransomware and malware attacks undertaken by groups with greater degrees of sophistication that wield it to inflict greater damage, and exacting greater prices.
Dr. Nate Evans, lead cybersecurity researcher with Argonne National Laboratory, has spent decades examining threats, creating proactive defensive solutions, and advising organizations on resiliency. “One thing we’ve seen change is the growth of the nation-state actor and the proliferation of groups with advanced capabilities tied to various nation states,” he observed in an exclusive interview with West Monroe. “Attackers are more advanced and very well-funded in some cases— and this is very different than how it was five years ago.”
Ransomware damages are predicted to cost the world economy $11.5 billion in 2019. ”
Dr. Evans’ observation is echoed in one of the most infamous cybersecurity breaches to strike U.S. utilities and electric grid infrastructure.
The unprecedented 2017–2018 cyberattacks perpetrated by Russian state actors revealed substantial weaknesses in the U.S. electric grid. The sophisticated, coordinated, well-funded attacks targeted hundreds of small contractors in the utility space, ultimately working their way up the supply chain and worming into dozens of larger utilities. While no lasting structural damage or service interruptions took place, the obvious motives to destabilize and prove that critical systems can be accessed continues to haunt utilities and government agencies.
All of this leads up to the fact that the financial impacts for global business are devastating. Global ransomware damages exceeded $5 billion in 2017, up more than 15 times the costs from 2015. Ransomware damages are predicted to cost the world economy $11.5 billion in 2019.
Chapter 3: Taking a fresh approach to cybersecurity requires leadership, culture change, and a companywide commitment
A fresh approach: From siloed IT department to full business operations effort
Despite the escalated rate and severity of cyberattacks, leaders at most companies have not changed their approach to cybersecurity in the past few years to adapt to this new and increasingly challenging environment.
When asked what he saw as the biggest mistake company directors are making, Stephen Reynolds, a partner at law firm Ice Miller LLP and former software engineer, said, “If you are still thinking about cybersecurity as just an IT or infosec problem, you’re doing it wrong.”
As his law firm’s top cybersecurity lawyer, Reynolds has witnessed first-hand this lack of forward thinking. “One of the biggest mistakes I see companies making today is thinking you can just throw money or software around to solve the cybersecurity problem. It takes a true companywide effort and culture change to address properly.”
The truth is that there are many areas for improvement in most companies’ approaches to cybersecurity, including:
- Inadequate data backup procedures
- A lack of proper planning and preparation
- Incomplete or irregular outage tabletop and recovery drills
- Siloed teams without insight into system-wide operational dependencies
- A lack of high-level support from the C-level and board of directors
The solutions to the problem are not necessarily “cyber solutions” in that they don’t require buying additional software or hiring another engineer. To successfully build out a vision of cyber resiliency, the effort must include considerable time, thought, and investment into infrastructure, backup solutions, accurate mapping of network and dependencies, planning for the right redundancies, and continuous scenario planning with interdisciplinary teams of IT and business operators.
Anyone questioning the above strategy should understand by now that breaches come with costs that go far beyond the purview of the IT department. Properly preparing for and mitigating the damage caused by lost revenue, lost market share, marketing investments to restore trust, and hidden legal and technical costs of recovery needs to be prioritized at the highest levels of the company.
The good news is that thinking about cyber resiliency shouldn’t be wholly unfamiliar. As a best practice and staple of good governance, many firms engage in continuity planning when it comes to natural disasters or critical personnel. But this kind of thinking needs to spread to cybersecurity, which should be handled as a multi-faceted and company wide effort with engaged leaders setting a plan to maintain the highest levels of operational continuity.
A fresh approach: From hyper focus on data protection to holistic view of operations
Even organizations that have invested in cybersecurity and consider themselves ready to combat attacks often take too narrow a view of security. They focus exclusively on data protection and regulatory compliance at the expense of a truly holistic, evaluative approach to the interdependencies and vulnerabilities across all their business operations.
Look closely at recent breaches and you’ll see that cases involving the theft of customer data, with otherwise little- to-no business disruption effects, ultimately recovered quickly and maintained customer trust. Those involving significant interruption of business operations resulted in significant losses and serious reputational damage.
Many firms engage in continuity planning when it comes to natural disasters or critical personnel. But this kind of thinking needs to spread to cybersecurity. ”
The data-protection orientation aligns with conventional wisdom, which holds that consumers and businesses are most concerned with the security of their data. But the advent of social media has heralded a new consumer attitude about privacy—with people sharing more personal and sensitive information than ever before. It’s common now to see someone check into a hospital on social media or post openly about mental health issues online. GoFundMe pages have also become popular and include quite a bit of personal information and data. This information, shared freely by an individual, often constitutes the same records that hospital systems prioritize keeping safe.
In surveys, consumers still voice major concerns about data privacy, but in practice, we observe that they’re more concerned about service disruption than breaches involving their personal data. If you’re not convinced, consider that consumers continue to shop at Target, book hotels at Starwood-Marriott, and post personal details on Facebook—despite highly publicized breaches involving personal information.
Consider your own assumptions and attitudes as a consumer on the issue of data security. Which would be more important: a hospital ready to care for your loved one or a hospital that protected your data?
Consumer advocacy group Privacy Rights Clearinghouse estimates that over 11 billion U.S. records have been compromised. If personal data theft was the most important driver of cyber insurance, we would see much more identity theft and individual liability. One reason we don’t is because so much personal data is already out there, there is a well-established cadre of credit reporting agencies and financial institutions already primed to intercede and identify fraudulent activity.
“I’ve seen a shift so that now the hackers are trying to go right after the money. If you think about it, SSNs are already out there,” said Reynolds, the attorney. “There is so much personal data already out there, so the value of trying to steal that information and sell it has decreased. Ransomware is a more direct, efficient way for cyber criminals to get what they’re after.”
A fresh approach: From short-term fixes to a long-term strategy that requires leadership commitment
Instead of responding crisis to crisis, leadership teams must take a farsighted view and recognize the question of cybersecurity and resilience for what it is—a foremost priority for long-term investment. It’s as critical to a business’ long-term success as careful management of the budget.
Dr. Nate Evans has spent decades examining threats, programming defensive solutions, and advising organizations on resiliency.
“What a lot of organizations haven’t looked at enough is the true cost of recovery,” said Nate Evans, a national laboratory researcher. “In the recovery phase, there’s a big investment of time and money that’s needed for the forensic investigation to find out what happened. You have to figure out what happened in order to truly fix it [and] that requires forensic tools and analysts. There is a gap in funds available, a gap in the skilled workforce, and a gap in the expectation of how much time a proper investigation will take.”
Consider ways to improve communication as a means of facilitating the right actions and investments. By nature, boards and executive teams are concerned by what they can’t see or don’t understand. Are they asking the right questions? How can your IT and operational teams do a better job of presenting information and risks in business terms? How will you be able to secure the necessary funds for consistent, long-term investments for resiliency?
Finally, and perhaps most significantly, adopting a cyber resiliency mindset will have you reconfiguring teams, creating new action plans, and implementing regular system tests and drills. Resilience is about redundancy and protection, often at the cost of convenience. It is inconvenient for employees to log in with multi-factor authentication but doing so reduces the company’s risk substantially.
In many ways cyber resiliency calls for complete culture change. And yes, that is intimidating. But now is the time to start making the moves that will fully protect your business—and we have some ideas to get you started.
A fresh approach: From periodic penetration testing to a 24/7 task
Start addressing the gaps revealed during scenario planning, and figure out a plan and priority to deal with them. For example, if you run a hospital you might print backup records of each admitted patient so that treatment can be ongoing for active patients even if your Electronic Health Record (EHR) system is down. More broadly, think through your backups—what data is critical, where is it stored, and how can you optimize for availability of data? Keep in mind that attackers often prioritize finding and encrypting backups as their first tactic to make victims more likely to pay the ransom.
Plan for and run a full-scale test to practice shutting down different data systems and getting the backups in place. Document the dependencies. Planning scenarios should be done at least annually—sometimes every six to nine months. The table-top security team should plan to move from theoretical discussion into real drills to test. Every time aspects of the business change (new manufacturing system, different logistics supplier, etc.)—the table-top plan should also adjust.
In the recovery phase, there’s a big investment of time and money that’s needed for the forensic investigation to find out what happened.” – Nate Evans, Cyber Analysis & Research Lead, Argonne National Laboratory. ”
Brian Robb, Underwriting Director in CNA Insurance’s cyber department, has been involved in the cyber insurance field for seven years. He shared his view on what an ongoing commitment to a resilience business model looks like: “A commitment to creating a resilient business model is a necessity. It is not as simple as running a penetration test or buying and installing a state-of-the-art firewall. These are absolutely great things to do from a cybersecurity standpoint, but an organization needs to establish business continuity plans, disaster recovery plans, and plans to respond when an incident occurs. These plans need to be tested regularly, and updated as the threat landscape changes. Creating a resilient business model really is a 24/7/365 task.”
Conclusion
Let’s return to our outage scenario from the beginning.
A breach has occurred. The website is down. You aren’t able to complete transactions, manufacture goods, serve customers, or even email a co-worker. Information trickles in from the IT team, and you’re likely facing sophisticated malware. Your team turns to you for leadership—what should they do? What should you do?
In one scenario, your team is prepared and supported by your company’s ongoing resiliency strategy and protocol. You know exactly what to do, because you have trained, practiced, and prepared for this exact moment. In a different scenario, you scramble in real time to respond amid chaos and confusion.
Clearly, a team executing a plan that has been practiced and adapted over time will be able to recover and return to business operations in the shortest possible time frame. The team left to scramble and work on-the-fly will face a much longer, daunting, and costly road that could take weeks or longer to recover.